DevOps is a quickly growing practice for companies in almost every market. With the influx of cyber attacks over the past decade, security has slowly crept forward in the SDLC to the point where we’re now hearing the term DevSecOps in developer circles.
To keep things tidy and help developers manage additional security responsibilities, tools for static and dynamic application security testing (SAST and DAST) have made their way into the fray. In this post, we’ll explain what SAST and DAST are, how they fit into developers’ workflows, and when they should be used.
What is application security testing (AST)?
Application security testing (AST) refers to the process of testing code to make sure it is free of vulnerabilities. There are many ways to test code, though static application security testing (SAST) and dynamic application security testing (DAST) are two of the more well-known options.
Application security testing has traditionally been a manual (and time-consuming) process, but the growing popularity of DevOps and the risk of insecure code have driven the majority of development teams to automate at least some of the processes. These days, most organizations use a variety of security testing tools to complete AST.
What are SAST and DAST?
What are SAST and DAST? As previously mentioned, under the AST umbrella, there live two different security testing approaches: SAST and DAST. Though different, neither is better than the other and the security testing outcome is superior when both are used together to detect security vulnerabilities in web applications and source code. SAST is a security testing approach that is performed on the application's code, while DAST is an approach that is performed on the running application. Both SAST and DAST are essential components of a comprehensive security testing strategy for software applications.
In summary, SAST and DAST help to ensure that computer systems are both safe and secure. These security measures help make sure that information is protected from hackers and other people who may try to steal it. They are critical tools for successful DevSecOps. Each runs a set of automated tests, and both introduce security at the beginning of the software development lifecycle.
Static application security testing (SAST)
SAST can be used to analyze source code for known vulnerabilities – and is also a type of white box testing. The test will run before your code is deployed, ensuring that developers are alerted to fixes during the development phase. SAST can help remediate situations where your code has a potentially dangerous attribute in a class or unsafe code that can lead to unintended code execution.
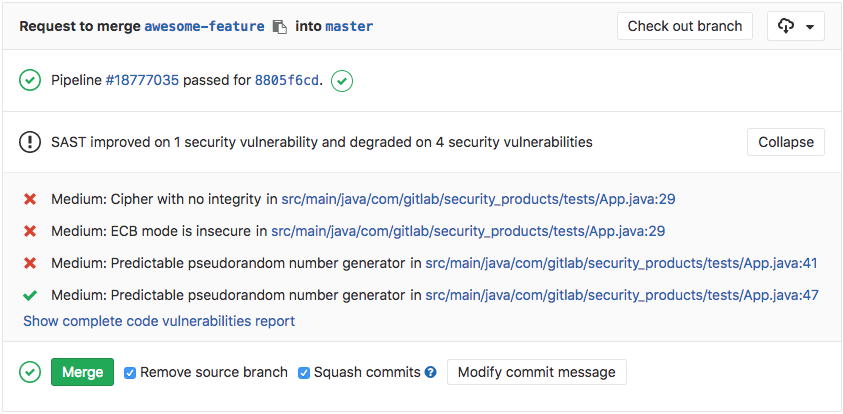
Within GitLab, SAST will automatically generate a summary of fixes and unresolved vulnerabilities following every code commit, but before your code is merged to the target branch. Tools that allow SAST reports to sit within the developer’s work interface enable ease of remediation and streamline testing procedures within the development phase.
SAST takes an inside-looking-out approach, looking for security problems that might have been missed during source code development. It is effective when used after development is complete but before the finished project (and any missed security vulnerabilities) is deployed. Lots of developers nowadays integrate SAST testing into their CI/CD pipelines.
Dynamic application security testing (DAST)
DAST, a type of black box testing, analyzes your running web applications or known runtime vulnerabilities. GitLab’s DAST tool runs live attacks on a review app during QA, meaning developers can iterate on new apps and updates earlier and faster.
As with SAST, DAST should auto-run so that the developer doesn’t have to take measures to initiate the test. In other situations, DAST can also be used to continuously monitor live web applications for issues like cross-site scripting or broken authentication flaws. Test results should inform developers of potential vulnerabilities and serve as a catalyst for ongoing updates.
DAST tools help you see your web application through the eyes of a hacker in a deployed environment. It constantly scans for security vulnerabilities during web application runtime, as well as checking the other API or web services that your application connects to. This makes DAST excellent for testing your complete IT environment where your application or web services run.
Test early and often using SAST and DAST
Static and dynamic application security testing are two helpful tools to keep your code secure, but don’t rely on them to handle all of your security needs. It’s still important to do manual code reviews, test high-level behaviors and functionality, conduct database scanning, and ensure that your whole team is operating with a security-first mindset.
Cover image by Mikael Kristenson on Unsplash



