This blog post contains information related to upcoming products, features, and functionality. It is important to note that the information presented is for informational purposes only.
Please do not rely on this information for purchasing or planning purposes.
As with all projects, the items mentioned in the blog post and linked pages are subject to change or delay. The development, release, and timing of products, features, or functionality remain at the sole discretion of GitLab, Inc.
Compliance and risk management have become the responsibility of everyone in an organization, and DevOps is no exception. To ensure the greatest level of security with the least exposure, business leaders must be able to trust that when they adopt or create compliance frameworks and policies, the associated rules will be able to be automatically deployed and enforced throughout the software development lifecycle. GitLab’s newest functionality and our near-term roadmap will help companies shift compliance left just as they have done for security, and also simplify governance and risk management across the entire software lifecycle.
Software supply chain risks
High-profile attacks on software supply chains, and the resulting demand for tighter controls in software development and deployment by the U.S. government and customers worldwide, have put compliance and risk management front and center. Companies are not only struggling to protect their traditional architecture, but cloud-native transformation has introduced new attack surfaces that require DevSecOps teams to secure more than just the code. Containers, orchestrators, microservices, and the cloud environment as a whole make the job of identifying and mitigating vulnerabilities and risks even more challenging.
Traditional application security is no longer enough in the era of DevOps automation and growth of cloud-native applications. In addition to testing and monitoring the new attack surfaces, complicated toolchains full of disparate products make it difficult to gain the visibility necessary to meet compliance demands and manage risk.
At GitLab, we remain focused on innovating an end-to-end DevOps Platform that organizations can leverage to simplify all aspects of security, compliance, governance, and risk management – no matter if you are developing software in a traditional environment, a cloud-native workspace, or a hybrid of the two.
Security and compliance remain key focuses for our product investment. Let’s take a quick look at recent innovations along with what’s coming in the near-term within the three themes of:
- Enabling secure cloud-native development
- Security governance
- Leveraging the DevOps Platform for better security and compliance
All of the information from these additional scans is available within existing workflows so DevSecOps teams can get the actionable insight they need to quickly find and fix issues from within the continuous integration (CI) pipeline. Here is how it looks for the developer:
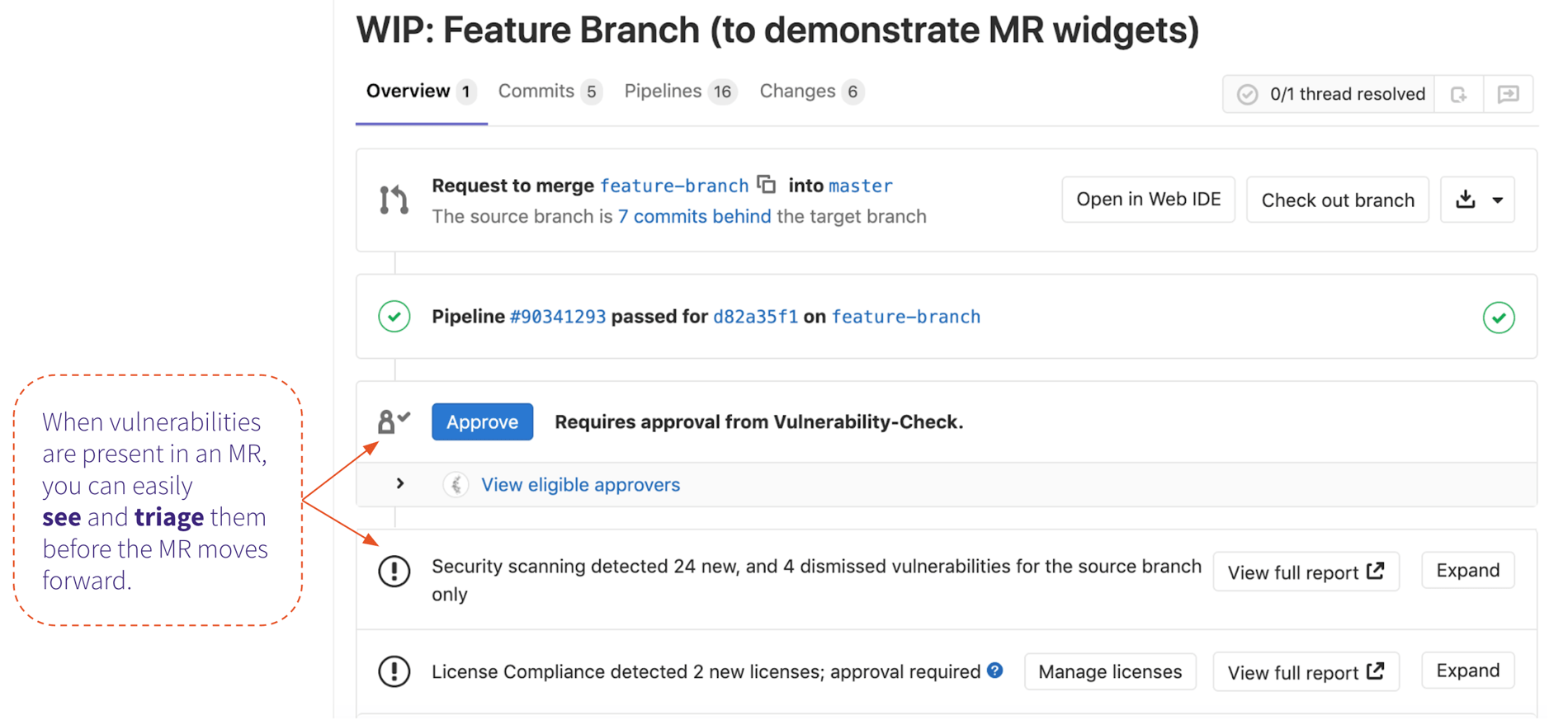
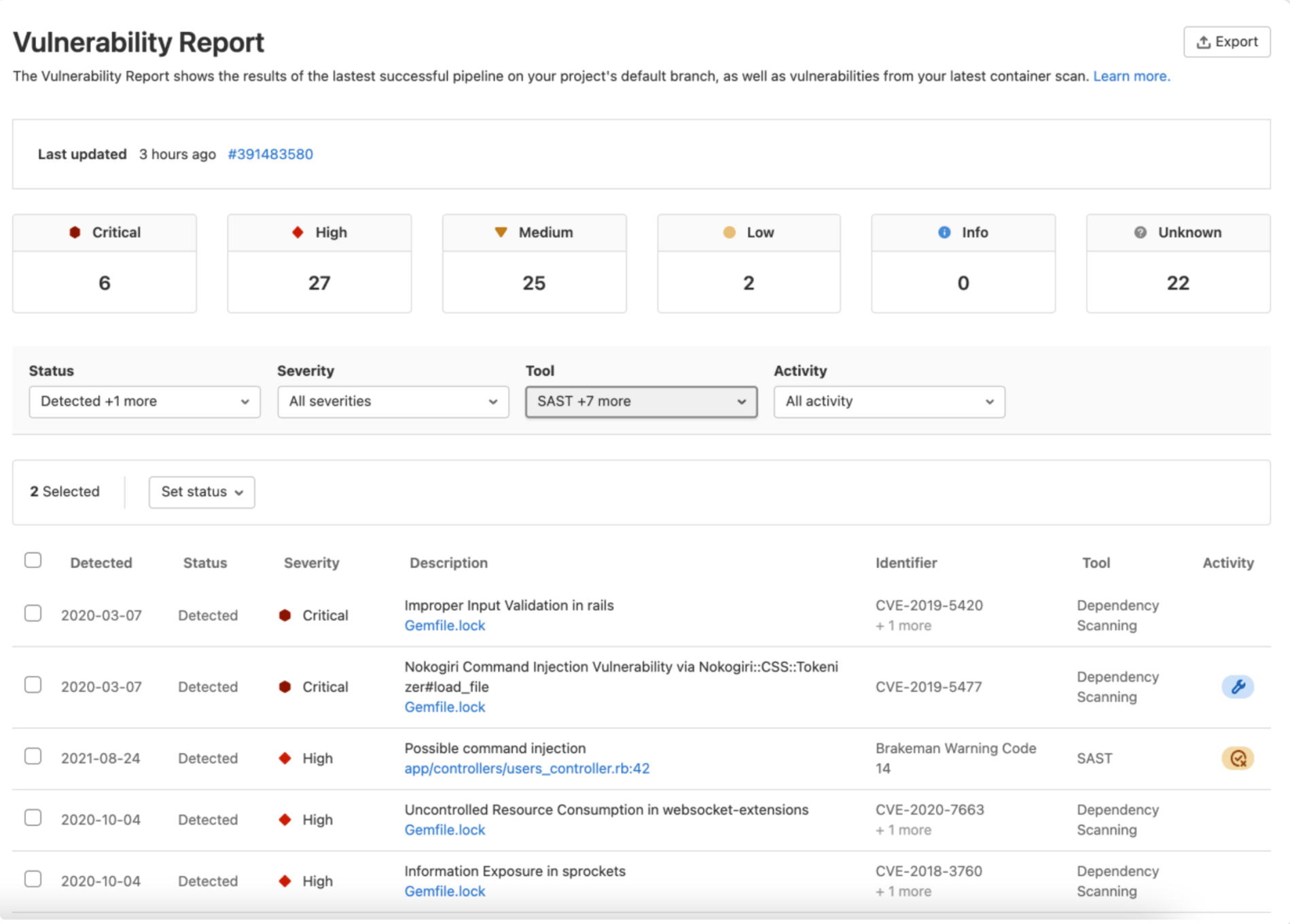
At the same time, security pros get early insight into risks as vulnerabilities are merged into feature branches (pre-production). The vulnerability report helps review and triage of vulnerabilities not resolved by the developer. This information is available at the project and group levels.
These capabilities are part of the existing GitLab Ultimate tier – no integrations or added costs required.
Enabling secure cloud-native development
Here’s what’s new in GitLab to help DevSecOps secure cloud-native development:
Infrastructure as code scanning – Many DevSecOps teams have started to implement IaC as part of their software development lifecycle, so GitLab has introduced robust scanning tools that can analyze the IaC configuration files (i.e., YAML, Kubernetes, CloudFormation, Terraform) to identify common security issues of these new attack surfaces.
More flexible container scanning – While we already had container scanning available in GitLab, we have switched to Trivy open-source container vulnerability scanner technology for pre-production environments. Trivy covers more languages and has better results than previous scanners. We also are beta-testing container scanning for production environments and cluster image scanning.
API security – APIs represent a tremendous attack surface when not properly secured. We are using the state-of-the-art fuzzing technology acquired from Peach Tech and Fuzzit to test APIs. In addition, our dynamic application security testing for APIs (DAST) is in beta.
Results from all of the scanners (IaC, containers and APIs) are incorporated into GitLab’s CI pipeline alongside other scan results enabling correction before configuration errors manifest in production.
Here’s what’s next that will help DevSecOps secure cloud-native development:
Production container scanning – We plan to make production container scanning generally available to scan containers for vulnerabilities after they’ve already been deployed. This will help surface vulnerabilities from new exploits not tested for during development.
DAST API scanner – We will be making our DAST API scanner generally available to enable broader coverage, better quality, and easier configuration. This will help you apply even greater defense-in-depth.
API Discovery – DevSecOps teams will be able to leverage access to code to automatically discover and test the APIs being used throughout the organization’s software supply chain. Understanding the attack surface is important to protecting it.
Security governance
Here’s what’s new to help organizations establish and manage security and compliance guardrails that allow developers to run fast while also managing risk:
Continuous compliance – Organizations can shift compliance left, similar to security, to identify and mitigate violations early on to avoid delays at go-live. Compliant workflow automation enables a DevOps admin to assign a compliance framework to a project and enforce scans and other common controls across all project pipelines. Developers may not easily sidestep required controls.
Policy Engine – GitLab automates a comprehensive set of security and compliance scans within the CI pipeline. Automating what happens when exceptions are encountered has been fairly simplistic. Now, GitLab provides users with a policy editor that provides more fine-grained rules that can determine what approvals are required helping you manage your own unique appetite for risk.
The policy engine is part of a larger direction for Security Orchestration that includes continued iteration on Security Alert Management, Security Policy Management, and Security Approvals.
Here’s what’s next that will help organizations establish and manage security governance:
Compliance checks in MRs – GitLab is further automating continuous compliance checks into the developer’s daily workflow in a similar way as security scans. This will help compliance essentially shift left so developers can find and fix compliance violations early and stay on schedule.
Governance at the group level – We are working to bring the controls found at the project level up to the group level so that policies may be more easily applied across a broad set of projects. This project is tied to the completion of workspaces.
The benefits of a single DevOps Platform
Here’s what’s new that enables you to leverage the benefits of a single DevOps Platform in GitLab’s Ultimate version:
Unified vulnerability management and reporting – We’ve consolidated security findings into a single dashboard that aggregates information from GitLab and other sources, including third-party scanners, our security partners, and more. You can pull in vulnerability data from other systems, manual pen testing, bug bounty programs, or even from security tools that don’t run in GitLab pipeline jobs. Vulnerability management in GitLab Ultimate helps you manage all of your software vulnerability information in one place to efficiently triage and remediate findings.
Proprietary SAST scanner – We have replaced some of our language-specific open-source scanners (OSS) with Semgrep, a proprietary scanner, to improve coverage, accuracy, and speed. Semgrep's flexible rule syntax is ideal for streamlining the GitLab Custom Rulesets feature for extending and modifying detection rules. It also allows GitLab customers access to Semgrep's community rules.
Here’s what’s next that will enable organizations to leverage the benefits of a single DevOps Platform in GitLab’s Ultimate version:
Software supply chain security – Organizations will be able to secure the full software supply chain with one application while improving confidence in its integrity and security. GitLab has put together a framework describing the various aspects that are required to accomplish this based on feedback from customers, inspiration from common standards (such as SLSA), as well as thought leadership from industry analysts. We would love your thoughts and contributions to these epics. Check out our Software Supply Chain Security direction page.
Inline security training – Developers will have just-in-time access to popular third-party security training as they encounter vulnerabilities. For instance, if a vulnerability is detected, a module will pop up that the developer can click on to learn more, including what the vulnerability is and how to fix it. This optimizes security training with an immediate need. More details coming soon.
Intelligent code security – Leveraging a previous acquisition, GitLab plans to help organizations automatically detect and remediate insecure coding practices using machine learning. This will help our customers further reduce risk and technical debt.
GitLab is uniquely transparent. By making our product roadmaps public, we encourage contribution and iteration. We invite you to contribute your ideas by checking out our product directions pages and commenting on upcoming releases.




