Published on: August 20, 2021
5 min read
How a new integration helps GitLab customers secure their code
GitLab Ultimate customers can use CodeSonar from GrammaTech for SAST and to bake protection into every stage of software development.

Software development teams that embrace agile and DevSecOps are able to code with a security-first mindset, which is essential for industries that build particularly complicated products where security is paramount, like: Aerospace and defense, automotive, industrial controls, medical devices, and more.
Static application security testing (SAST) solutions, like CodeSonar® from GrammaTech, integrate directly into CI/CD pipelines to bake security into every step of the software development life cycle (SDLC) – protecting your products every step of the way. Security solutions like GrammaTech pair well with an all-in-one DevOps Platform like GitLab, and allow development teams to follow best practices and industry standards to develop code that is better quality and more secure.
The GrammaTech and GitLab integration
The GrammaTech module for GitLab Ultimate provides native SAST capabilities that scan code for defects in CI/CD pipelines and eliminates the need for any integration and maintenance by users. It allows developers to assess code continuously, avoiding costly mistakes and the duplicative work associated with waiting until the testing phase to scan for security problems.
We recognize that developers face pressure to meet aggressive deadlines for delivering new software, as rolling releases and agile development practices have developers pushing new features and code into production faster. Integrating SAST tools like CodeSonar into a DevOps Platform like GitLab Ultimate is a natural consequence to more iterative development in companies that embrace DevSecOps practices. CodeSonar helps developers shift security left by detecting and eliminating bugs and vulnerabilities at the earliest stages of the SDLC.
SAST with CodeSonar
CodeSonar uses a unified data flow and symbolic execution analysis to examine the computation of the complete application. This approach is deeper than typical pattern-matching syntax analysis, and discovers 3-5x more defects on average.
Static analysis is unlike other software development tools (i.e., testing tools, compilers, and configuration management) becuase it can be integrated into the development process at any time with ease. CodeSonar simply attaches to your existing build environments to add analysis information to your verification process.
How does CodeSonar work?
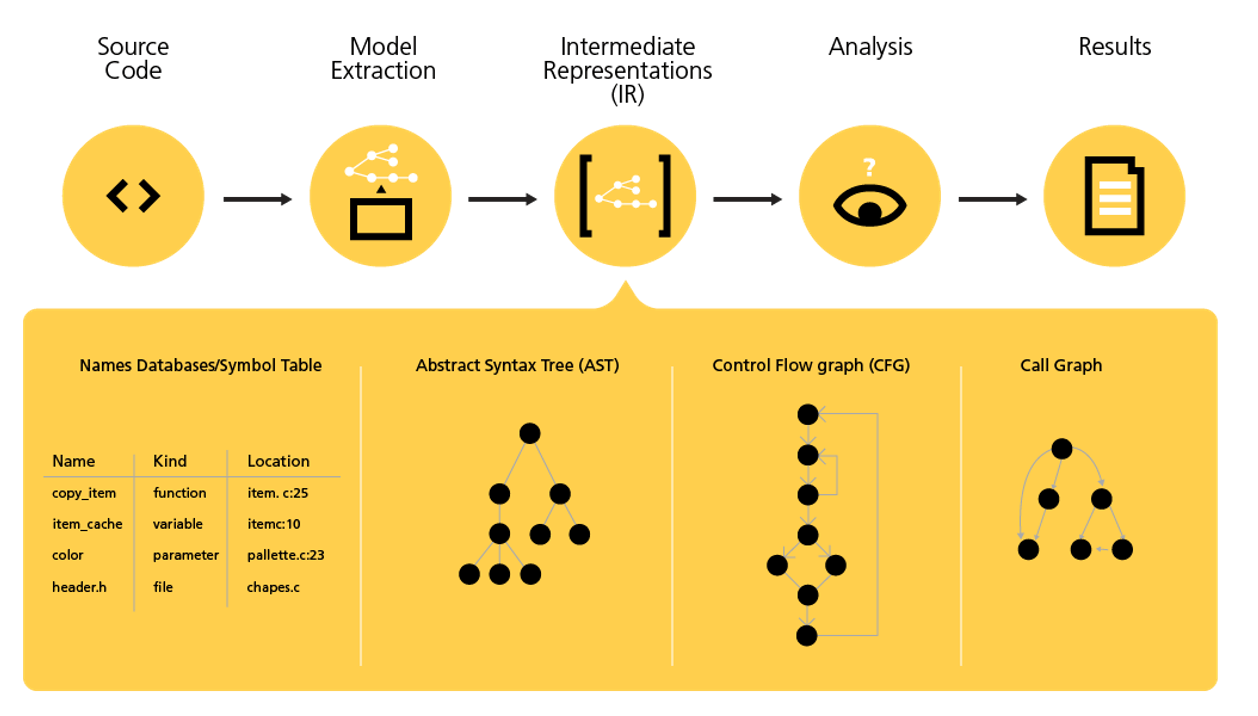
Like a compiler, CodeSonar does a "build" of your code using the existing build environment, but instead of creating object code, CodeSonar creates an abstract model of your entire program. From the derived model, CodeSonar's symbolic execution engine explores program paths, reasoning about program variables, and how they relate. Advanced theorem-proving technology prunes infeasible program paths from the exploration.
 See how CodeSonar secures code.
See how CodeSonar secures code.
Checkers in CodeSonar perform static code analysis to find common defects, violations of policies, etc. Checkers operate by traversing or querying the model and looking for particular properties or patterns that indicate defects. Sophisticated symbolic execution techniques explore paths through a control-flow graph – the data structure representing paths that might be traversed by a program during its execution. When the path exploration notices an anomaly, a warning is generated.
An astronomical number of combinations of circumstances must be modeled and explored, so CodeSonar employs a variety of strategies to ensure scalability. For example, procedure summaries are refined and compacted during the analysis, and paths are explored in a way that minimizes paging.
Continuous Integration enabled by GitLab
Integrating CodeSonar into GitLab's pipeline is done with each merge request (MR), automatically analyzing your code and returning any vulnerabilities found via the GitLab SAST interface. Users can consult the GitLab Security Dashboard to get an overview of code security, and the Vulnerability Report gets into the details.
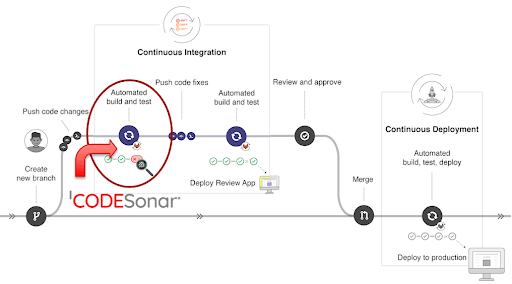 How CodeSonar integrates with GitLab CI pipelines.
How CodeSonar integrates with GitLab CI pipelines.
Review CodeSonar warnings in GitLab Vulnerability Reports
CodeSonar displays vulnerabilities right in the GitLab UI – you can review a warning, create a GitLab issue, and assign it to a developer – all in a single application. You can also dismiss vulnerabilities. CodeSonar's fingerprinting technology ensures that GitLab won't ever show dismissed vulnerabilities to you again.
Get a more detailed warning view
Sometimes you need more information to decide how to handle a particular warning. CodeSonar and GitLab make this easy. The CodeSonar warning message can be viewed directly in GitLab, and CodeSonar's detailed warning reports with annotated source code are just a click away – no copy and pasting, or searching for line numbers.
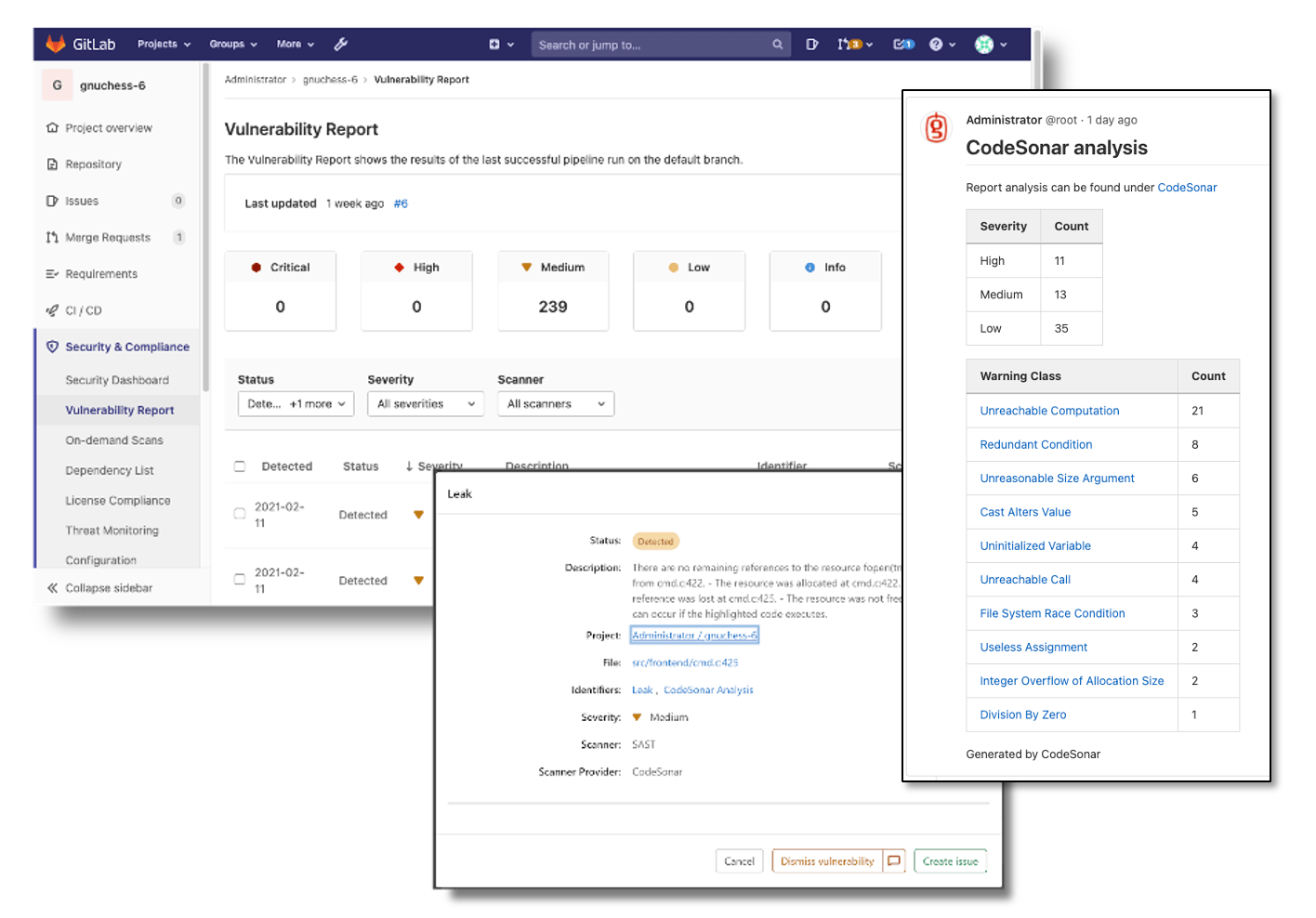 See example of a GitLab vulnerability report and detailed view of warnings.
See example of a GitLab vulnerability report and detailed view of warnings.
How to get started
A typical way to use the GitLab CI/CD pipeline is to set it up to run whenever new Git commits are submitted to a MR. When you add CodeSonar static analysis to your MR pipeline, GitLab will display the new analysis warnings on the MR page. The full set of warnings is always available on the pipeline page.
Prerequisites to use CodeSonar
- The CodeSonar integration requires a working instance of GitLab Ultimate edition.
- You must have a source code project in your GitLab instance that you wish to analyze. Set up a GitLab CI/CD pipeline for your project that can build your source code. This will include the configuration of one or more GitLab pipeline jobs (more on how to configure GitLab Runners).
- If you use Docker, ensure you have Docker Engine version 19.03.12 or later.
- Use the CodeSonar software package that is appropriate for your GitLab pipeline job runner's operating platform.
- Set up a dedicated, "persistent" CodeSonar Hub to coordinate and receive the results of your analysis. See your CodeSonar manual for how to set up and license a Hub.
- You will need a valid CodeSonar Hub license that is appropriate to your configuration and the CodeSonar GitLab Integration software package.
Read the instructions on installing the CodeSonar GitLab integration.
Christian Simko is the Director of Product Marketing at GrammaTech.
We want to hear from you
Enjoyed reading this blog post or have questions or feedback? Share your thoughts by creating a new topic in the GitLab community forum.
Share your feedback