Published on: August 26, 2025
2 min read
Fine-grained permissions for job tokens is now GA
GitLab now allows the use of fine-grained permissions for CI/CD job tokens, enhancing the security of your software supply chain.

CI/CD pipelines often inherit overprivileged permissions from user accounts, creating significant security risks if pipelines are compromised or tokens are leaked. GitLab 18.3 introduces fine-grained permissions for job tokens to solve this problem, moving this security enhancement from Beta to GA.
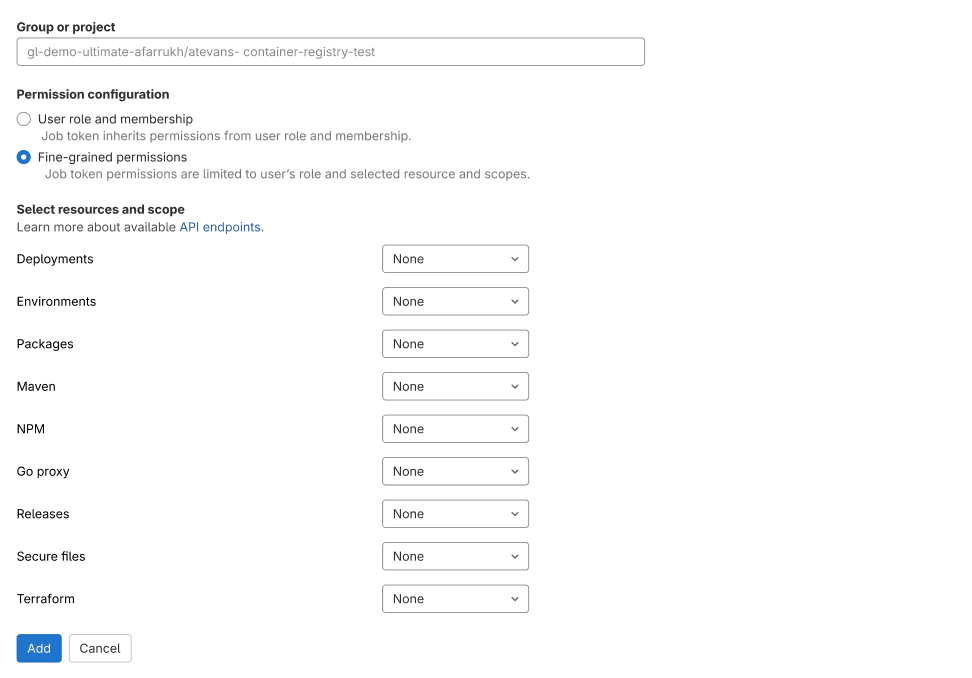
This capability allows maintainers to implement granular permissions that control job token access to API resources. Following the principle of least privilege, these job tokens have no ability to access any API resources until you explicitly grant them permissions.
This initial release includes fine-grained permissions for the following resources:
- Repositories
- Deployments
- Environments
- Jobs
- Packages
- Pipelines
- Releases
- Secure Files
- Terraform State
Additional API endpoints are planned for future releases. For more information, see the associated epic.
The bigger picture
This release represents a critical step in GitLab's broader mission to improve your software supply chain security. Historically, job tokens have been bound to the user running the pipeline, inheriting their privileges and creating security risks if pipelines are compromised.
Fine-grained permissions for job tokens provide a foundation for a more secure CI/CD ecosystem that:
- Reduces attack surface: Implements the principle of least privilege by limiting access to only necessary resources
- Eliminates dependency on long-lived tokens: Provides a secure alternative that reduces the need for personal access tokens and other persistent credentials
- Prepares for machine-based identity: This opt-in approach lays the groundwork for eventually decoupling job tokens from user identities entirely, moving toward true machine-to-machine authentication
- Enables secure automation at scale: Supports complex deployment workflows and CI/CD components without compromising security
Getting started
Security teams and DevOps engineers should evaluate this feature for any projects running automated deployments, package publishing, or infrastructure management. Since this is an opt-in capability, you can migrate gradually to minimize disruption to your existing pipelines.
Start by identifying your most critical pipelines and auditing their current permission requirements. Then enable fine-grained permissions and configure the minimal access needed for each project. For more information, see the documentation on fine-grained permissions for CI/CD job tokens.


