Published on: July 24, 2025
7 min read
Software supply chain security guide: Why organizations struggle
Part 1 of this new series explores fundamental challenges, practical solutions, and emerging trends, including AI, that every development team needs to understand.

Ask most development teams about supply chain security, and you'll get answers focused on vulnerability scanning or dependency management. While these are components of supply chain security, they represent a dangerously narrow view of a much broader challenge.
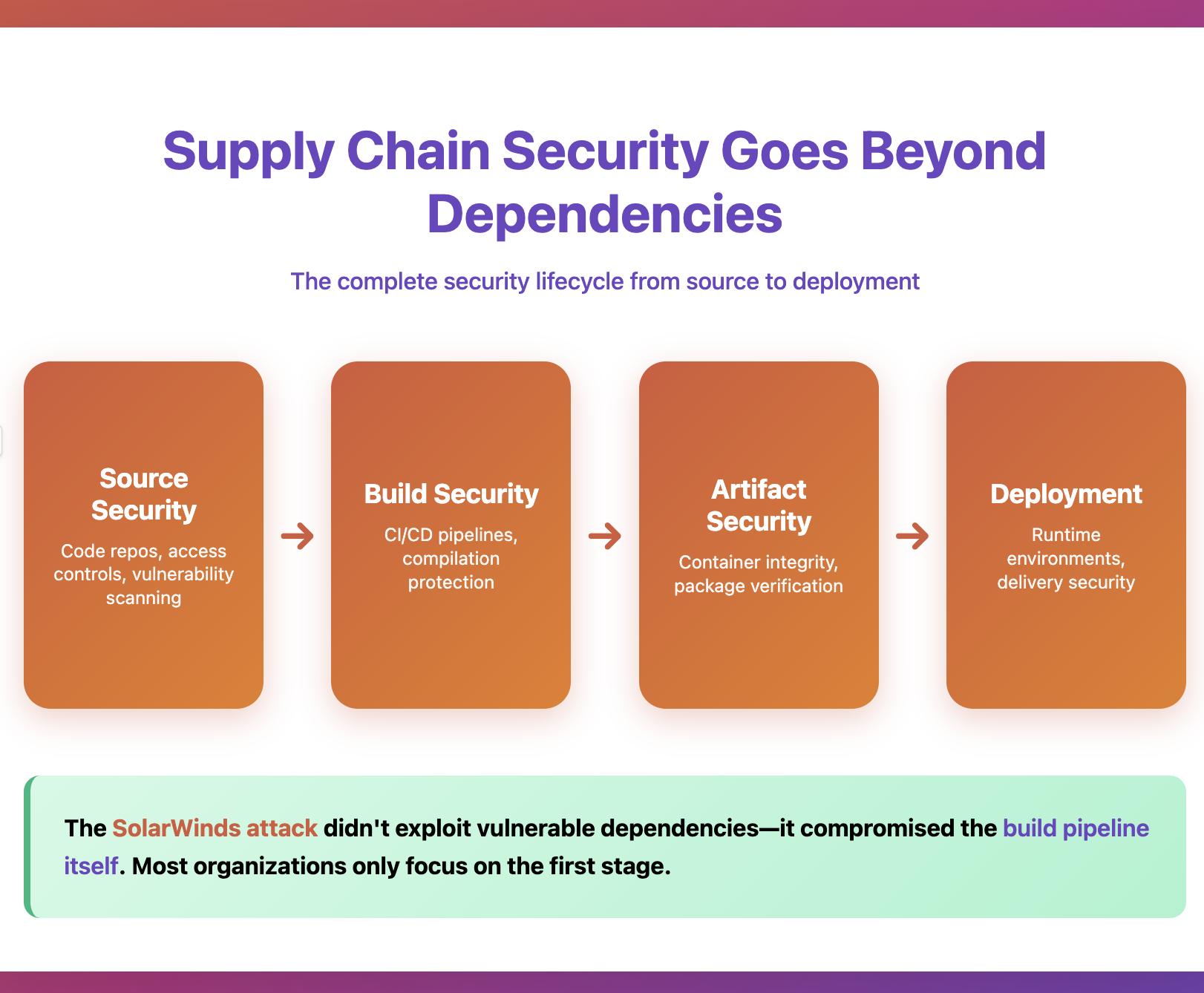
Supply chain security isn't just about scanning dependencies. It encompasses the entire journey from code creation to production deployment, including:
- Source security: protect code repositories, managing contributor access, ensuring code integrity
- Build security: secure build environments, preventing tampering during compilation and packaging
- Artifact security: ensure the integrity of containers, packages, and deployment artifacts
- Deployment security: secure the delivery mechanisms and runtime environments
- Tool security: harden the development tools and platforms themselves
The "chain" in supply chain security refers to this interconnected series of steps. A weakness anywhere in the chain can compromise the entire software delivery process.
The 2020 SolarWinds attack illustrates this perfectly. In what became one of the largest supply chain attacks in history, state-sponsored attackers compromised the build pipeline of SolarWinds' Orion network management software. Rather than exploiting a vulnerable dependency or hacking the final application, they injected malicious code during the compilation process itself.
The result was devastating: More than 18,000 organizations, including multiple U.S. government agencies, unknowingly installed backdoored software through normal software updates. The source code was clean, the final application appeared legitimate, but the build process had been weaponized. This attack remained undetected for months, demonstrating how supply chain vulnerabilities can bypass traditional security measures.
Common misconceptions that leave organizations vulnerable
Despite growing awareness of supply chain threats, many organizations remain exposed because they operate under fundamental misunderstandings about what software supply chain security actually entails. These misconceptions create dangerous blind spots:
- Thinking software supply chain security equals dependency scanning
- Focusing only on open source components while ignoring proprietary code risks
- Believing that code signing alone provides sufficient protection
- Assuming that secure coding practices eliminate supply chain risks
- Treating it as a security team problem rather than a development workflow challenge
How AI is changing the game
Just as organizations are grappling with traditional software supply chain security challenges, artificial intelligence (AI) is introducing entirely new attack vectors and amplifying existing ones in unprecedented ways.
AI-powered attacks: More sophisticated, more scalable
Attackers are using AI to automate vulnerability discovery, generate convincing social engineering attacks targeting developers, and systematically analyze public codebases for weaknesses. What once required manual effort can now be done at scale — with precision.
The AI development supply chain introduces new risks
AI is reshaping the entire development lifecycle, but it's also introducing significant security blind spots:
- Model supply chain attacks: Pre-trained models from sources like Hugging Face or GitHub may contain backdoors or poisoned training data.
- Insecure AI-generated code: Developers using AI coding assistants may unknowingly introduce vulnerable patterns or unsafe dependencies.
- Compromised AI toolchains: The infrastructure used to train, deploy, and manage AI models creates a new attack surface.
- Automated reconnaissance: AI enables attackers to scan entire ecosystems to identify high-impact supply chain targets.
- Shadow AI and unsanctioned tools: Developers may integrate external AI tools that haven't been vetted.
The result? AI doesn't just introduce new vulnerabilities, it amplifies the scale and impact of existing ones. Organizations can no longer rely on incremental improvements. The threat landscape is evolving faster than current security practices can adapt.

Why most organizations still struggle
Even organizations that understand supply chain security often fail to act effectively. The statistics reveal a troubling pattern of awareness without corresponding behavior change.
When Colonial Pipeline paid hackers $4.4 million in 2021 to restore operations, or when 18,000 organizations fell victim to the SolarWinds attack, the message was clear: Supply chain vulnerabilities can bring down critical infrastructure and compromise sensitive data at unprecedented scale.
Yet, despite this awareness, most organizations continue with business as usual. The real question isn't whether organizations care about supply chain security — it's why caring alone isn't translating into effective protection.
The answer lies in four critical barriers that prevent effective action:
1. The false economy mindset
Organizations sometimes focus on the cost instead of "what's the most effective approach?" This cost-first thinking creates expensive downstream problems.
2. Skills shortage reality
With organizations averaging 4 security professionals per 100 developers, according to BSIMM research, and 90% of organizations reporting critical cybersecurity skills gaps, according to ISC2, traditional approaches are mathematically impossible to scale.
3. Misaligned organizational incentives
Developer OKRs focus on feature velocity while security teams measure different outcomes. When C-suite priorities emphasize speed-to-market over security posture, friction becomes inevitable.
4. Tool complexity overload
The average enterprise uses 45 cybersecurity tools, with 40% of security alerts being false positives and must coordinate across 19 tools on average for each incident.
These barriers create a vicious cycle: Organizations recognize the threat, invest in security solutions, but implement them in ways that don't drive the desired outcomes.
The true price of supply chain insecurity
Supply chain attacks create risk and expenses that extend far beyond initial remediation. Understanding these hidden multipliers helps explain why prevention is not just preferable – it's essential for business continuity.
Time becomes the enemy
- Average time to identify and contain a supply chain breach: 277 days
- Customer trust rebuilding period: 2-3+ years
- Engineering hours diverted from product development to security remediation
Reputation damage compounds
When attackers compromise your supply chain, they don't just steal data – they undermine the foundation of customer trust. Customer churn rates typically increase 33% post-breach, while partner relationships require costly re-certification processes. Competitive positioning suffers as prospects choose alternatives perceived as "safer."
Regulatory reality bites
The regulatory landscape has fundamentally shifted. GDPR fines now average over $50 million for significant data breaches. The EU's new Cyber Resilience Act mandates supply chain transparency. U.S. federal contractors must provide software bills of materials (SBOMs) for all software purchases — a requirement that's rapidly spreading to private sector procurement.
Operational disruption multiplies
Beyond the direct costs, supply chain attacks create operational chaos such as platform downtime during attack remediation, emergency security audits across entire technology stacks, and legal costs from customer lawsuits and regulatory investigations.
What's wrong with current approaches
Most organizations confuse security activity with security impact. They deploy scanners, generate lengthy reports, and chase teams to address through manual follow-ups. But these efforts often backfire — creating more problems than they solve.
Massive scanning vs. effective protection
Enterprises generate over 10,000 security alerts each month, with the most active generating roughly 150,000 events per day. But 63% of these are false positives or low-priority noise. Security teams become overwhelmed and turn into bottlenecks instead of enablers.
The collaboration breakdown
The most secure organizations don't have the most tools; they have the strongest DevSecOps collaboration. But most current setups make this harder by splitting workflows across incompatible tools, failing to show developers security results in their environment, and offering no shared visibility into risk and business impact.
The path forward
Understanding these challenges is the first step toward building effective supply chain security. The organizations that succeed don't just add more security tools, they fundamentally rethink how security integrates with development workflows. They also review end-to-end software delivery workflows to simplify processes, reduce tools and improve collaboration.
At GitLab, we've seen how integrated DevSecOps platforms can address these challenges by bringing security directly into the development workflow. In our next article in this series, we'll explore how leading organizations are transforming their approach to supply chain security through developer-native solutions, AI-powered automation, and platforms that make security a natural part of building great software.
Learn more about GitLab's software supply chain security capabilities.

