Published on: October 22, 2024
8 min read
Quick vulnerability remediation with GitLab Advanced SAST + Duo AI
Shorten your mean time to remediation by pairing Advanced SAST and artificial intelligence. This detailed demo shows you how.

With GitLab 17.4, we’ve made GitLab Advanced SAST generally available. GitLab Advanced SAST is a static application security testing scanner designed to discover vulnerabilities by performing cross-function and cross-file taint analysis. By following the paths user inputs take, the analyzer identifies potential points where untrusted data can influence the execution of your application in unsafe ways, ensuring the vulnerabilities are detected even when they span multiple functions and files.
GitLab Advanced SAST can be used together with GitLab Duo Vulnerability Explanation in order to reduce the mean time to remediation (MTTR). GitLab Duo can provide practical, AI-powered examples of how threat actors can exploit vulnerabilities and offer light-weight remediation guidance, which can be used with cross-file analysis to enhance application security (AppSec) efficiency.
This tutorial will show you how to:
- enable GitLab Advanced SAST
- read results from the scanner
- review the code flow of a vulnerability
- use GitLab AI to quickly remediate the vulnerability
Enable GitLab Advanced SAST
Follow the instructions below to enable GitLab Advanced SAST. You can also view this video to get started:
Run GitLab Advanced SAST on each code commit
Before using Advanced SAST, the following prerequisites must be met:
- GitLab Ultimate Subscription (free trial)
- GitLab SaaS or GitLab Self-managed (running Version 17.4)
To enable the GitLab Advanced SAST scanner:
- On the left sidebar, select Search or Go to and find your project.
- Add or edit the
.gitlab-ci.ymlto include the following:- Test stage
Jobs/SAST.gitlab-ci.ymltemplateGITLAB_ADVANCED_SAST_ENABLEDvariable set to true
- Apply the change.
Your newly merged .gitlab-ci.yml should contain the following:
stages:
- test
include:
- template: Jobs/SAST.gitlab-ci.yml
variables:
GITLAB_ADVANCED_SAST_ENABLED: 'true'
This will now run the gitlab-advances-sast job within the test stage of your application along with all the other jobs you have defined. Advanced SAST will replace the semgrep SAST scanner for the supported programming languages.

Note: You can fully configure the job as you would any job in GitLab. For more information, see the CI/CD YAML syntax documentation.
Remediate vulnerabilities in merge request (pre-production)
Just like our previous SAST scanner, Advanced SAST allows you to scan source code in the diff of a feature branch. This allows us to address any incoming vulnerabilities before they make it into production. Here we can see the scanner results for the diff within a merge request:
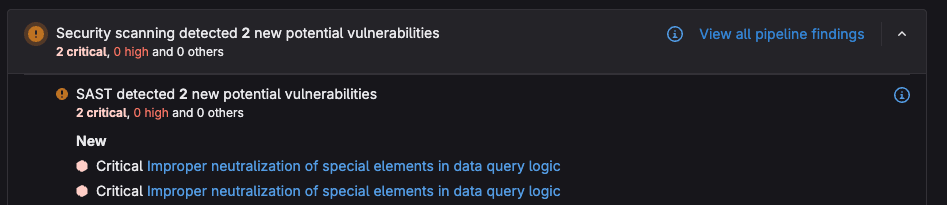
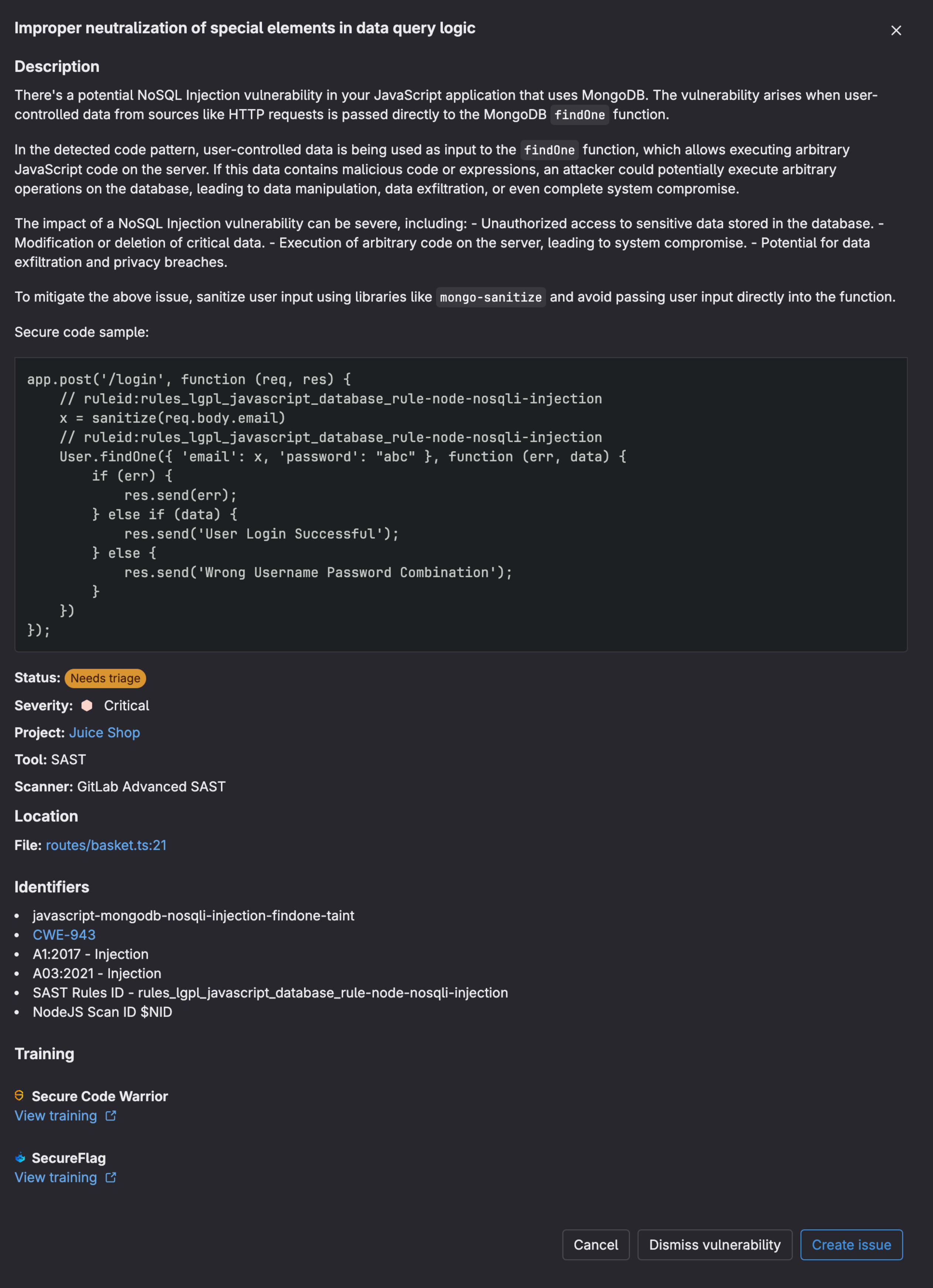
When selecting a newly detected vulnerability, we get the following details to assist with remediation:
- Status: The status of the vulnerability (Needs triage, Confirmed, Dismissed, Resolved)
- Description: Detailed information on the detected vulnerability
- Detection time: Time vulnerability was detected
- Location: Line of code where vulnerability is detected
- Severity: Severity of vulnerability from CVE database
- Training: Gamified training from our partners
- Solutions: Information on how to remediate or resolve a vulnerability
- Identifiers: Relevant links showcasing detailed description, exploitation, and remediation
Vulnerabilities detected within an MR are actionable, meaning they can be dismissed or an issue can be created and populated with relevant vulnerability information.
Dismissing an issue saves AppSec teams time, because they can see relevant developer information when reviewing an MR. Creating a confidential issue allows developers and AppSec teams to further collaborate on resolving a vulnerability where a fix is not straightforward. Confidential issues have limited permissions and can be used with confidential merge requests to prevent possible malicious actors from exploiting.
To further support separation of duties and prevent vulnerable code from making it into production, you can require approval from certain people (for example, the security team) in order to merge vulnerable code.
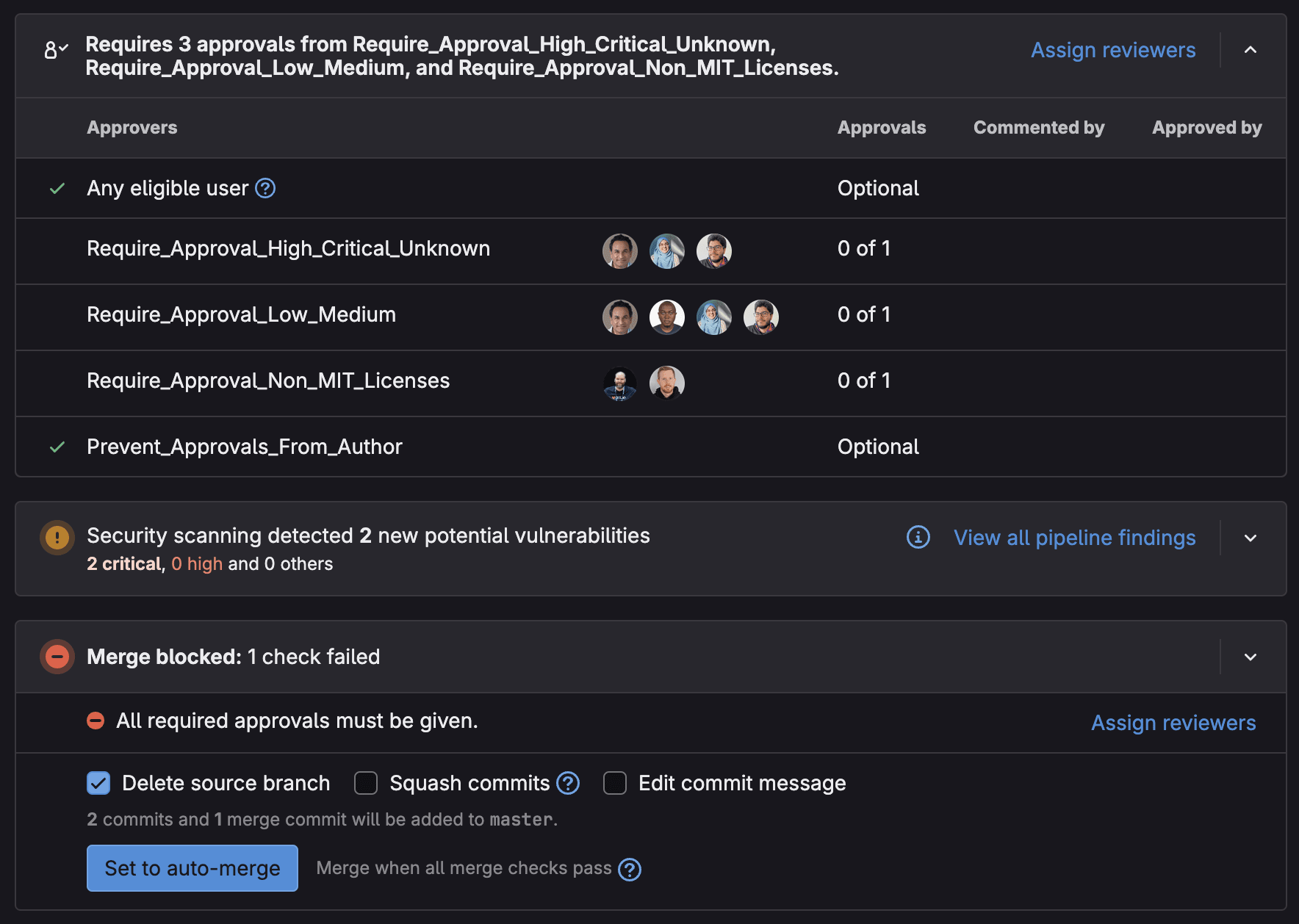
Note: Learn more about Security Policies and how to implement them in the Security Policy documentation.
Manage vulnerabilities in production
While preventing vulnerabilities from making it into production is crucial for application security, it is equally as important to manage vulnerabilities in production. When security scanners are run on a default or production-level branch, a vulnerability report will be populated with the latest vulnerability data which can be used to triage and manage vulnerabilities.

When selecting a vulnerability you get similar vulnerability details as seen in a merge request, making for a single source of truth for developers and AppSec teams.
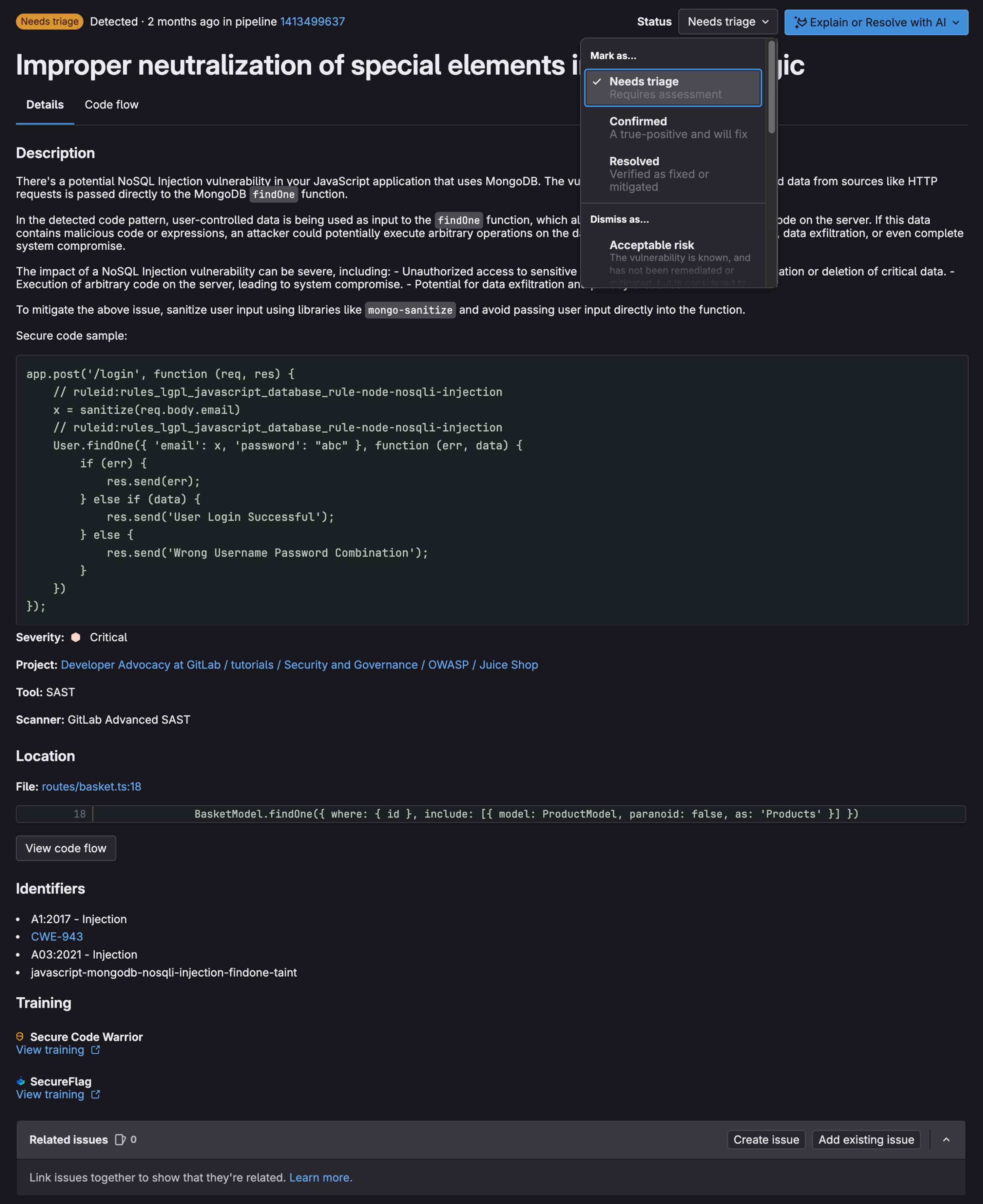
AppSec teams can triage a vulnerability by changing its status and adding relevant details on the status change. Issues can be created to track the progress of a fix. From here, a developer can be assigned.
Examine vulnerable code flow
For vulnerabilities detected with Advanced SAST, we can see a "Code flow" tab on the Vulnerability page.

In this example, you can see that a vulnerability is traced across multiple functions, giving deeper insight into the best practices we should put in place to not only resolve the vulnerability, but prevent similar vulnerabilities in the future.
Use GitLab Duo Vulnerability Explanation
GitLab Duo can help you mitigate or remediate a vulnerability by using a large language model to:
- Summarize the vulnerability
- Help developers and security analysts understand the vulnerability
- Show how the vulnerability can be exploited
- Provide a suggested remediation or mitigation
To use Vulnerability Explanation, the following is required:
- GitLab Ultimate subscription
- GitLab Duo Enterprise seat
- GitLab Duo must be enabled for your group or instance
From the vulnerability report, you can select a SAST vulnerability and go to its Vulnerability page. From the Vulnerability page, you can do any of the following to explain the vulnerability:
- Select the text below the vulnerability description
- You can use AI by asking GitLab Duo Chat to explain this vulnerability and offer a suggested fix.
- In the upper right, from the "Resolve with merge request" dropdown list, select Explain Vulnerability, then select Explain vulnerability.
- Open GitLab Duo Chat and use the explain a vulnerability command:
/vulnerability_explain.
Then the vulnerable code will be processed by Anthropic’s Claude 3 Haiku model and provide the following data:
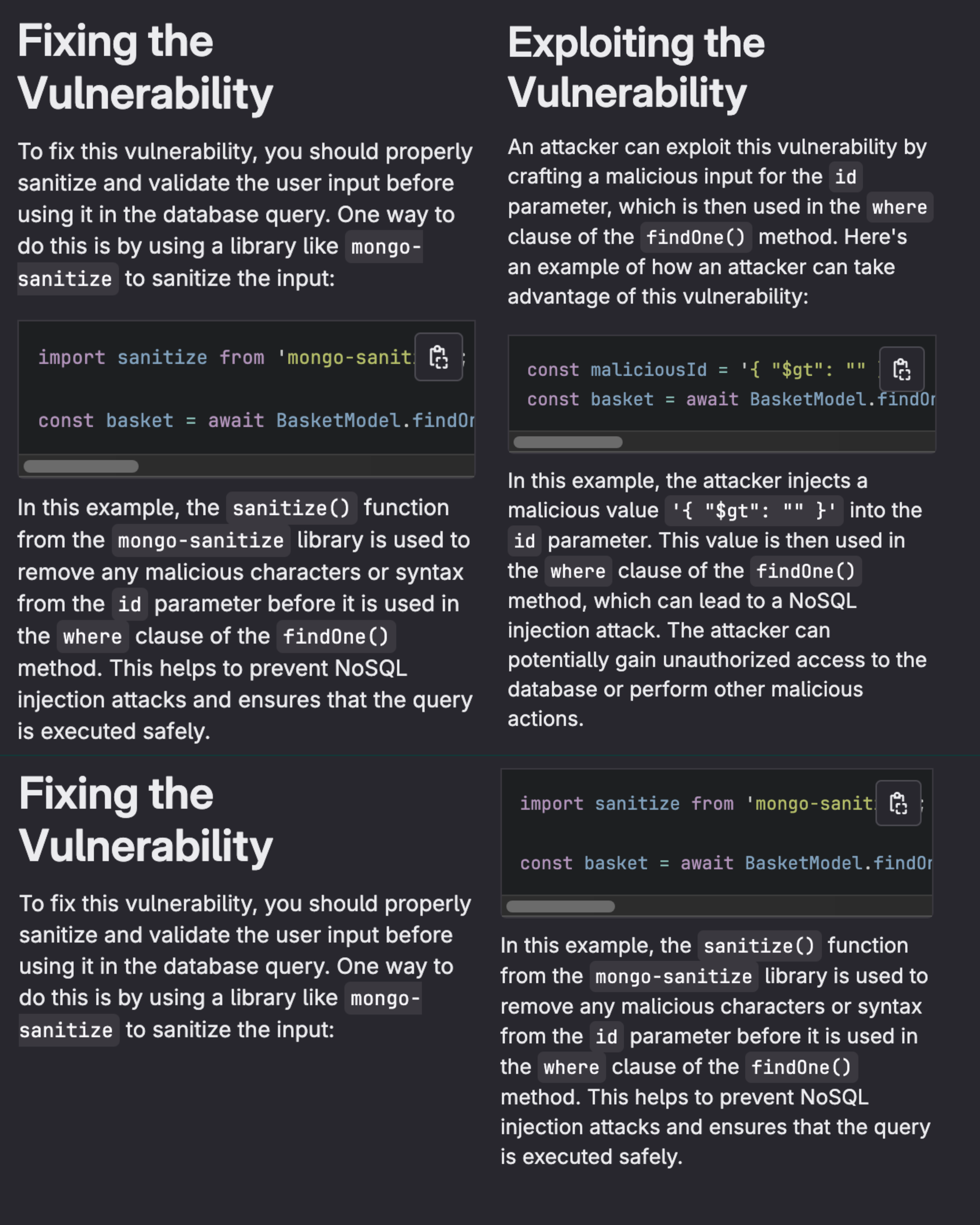
Putting it all together
Now, let's put it all together with a concrete example. I will use the OWASP Juice Shop as my demo application and run GitLab Advanced SAST to detect a vulnerability in production. Then I will use the vulnerability code flow and GitLab Duo to investigate vulnerability exploitation, and remediation. You can follow along with this demo and see this workflow in action by watching:
The detection and remediation workflow is as follows:
- Enable GitLab Advanced SAST and run it on the project’s default branch.
- Open the Vulnerability Report and sort by Tool:GitLab Advanced SAST.
- Select the Improper neutralization of special elements in data query logic vulnerability found in
Basket.ts. - Use the vulnerability code flow to understand the vulnerable paths.
- Run Explain this vulnerability to see exploit information.
- Run the application locally to attempt exploitation.
- Change vulnerability status to "Confirmed" and provide relevant info.
- Determine remediation path using all relevant data:
- Vulnerability page insights, Code Flow, Vulnerability Explanation results
- Create a new branch and apply remediation.
- Run the remediated application locally and try to exploit again.
- Create a merge request with the fix.
- Code change will be tested using CI to assure we don’t break the application.
- Validate and merge MR.
- Test exploit in deployed environment.
- Change vulnerability status to "Resolved" on the Vulnerability page.
Note: There are many ways to triage and remediate vulnerabilities, make sure to follow best practices set by your organization.
Useful links
To learn more about GitLab and how you can get started with enhancing your organization’s application security posture, check out the following resources.
- GitLab Ultimate
- GitLab Duo
- GitLab Security and Compliance Solutions
- GitLab Software Supply Chain Security Solutions
- GitLab Continuous Software Compliance
- JuiceShop Demo Application
- GitLab AppSec documentation
- Advanced SAST documentation
- Explain this Vulnerability documentation
- Code Flow documentation
- Security Policy documentation
- OWASP Juice Shop documentation

