Published on: January 22, 2025
7 min read
Guide to fulfilling SOC 2 security requirements with GitLab
Understand the application security features in the GitLab DevSecOps platform that map to System and Organization Controls 2 requirements.

For businesses that handle sensitive customer information, achieving SOC 2 (System and Organization Controls 2) compliance is not just a good practice — it's often a necessity. SOC 2 is a rigorous auditing standard developed by the American Institute of Certified Public Accountants that assesses a service organization's controls related to security, availability, processing integrity, confidentiality, and privacy.
While SOC 2 is not legally mandated, it has become increasingly important, in part due to breaches consistently seen in news headlines. Obtaining SOC 2 compliance allows customers to build trust with service organizations because they know their data is being properly stored and security controls have been assessed by a third party.
In this guide, we'll review the requirements for obtaining SOC 2 compliance and how GitLab can help your organization meet the highest standards for application security.
What requirements are set by SOC 2
The compliance process involves an audit by an independent auditor who evaluates the design and operating effectiveness of an organization's controls. This process can be very costly, and many organizations are not sufficiently prepared before an audit. With the SOC 2 audit process typically taking close to a year, it is important to establish an efficient pre-audit process.
To obtain SOC 2 compliance, an organization must meet requirements based on the Trust Services Criteria:
| Criteria | Requirements |
|---|---|
| Security | - Implement controls to protect against unauthorized access - Establish procedures for identifying and mitigating risks - Set up systems for detecting and addressing security incidents |
| Availability | - Ensure systems are accessible for operation as agreed - Monitor current usage and capacity - Identify and address environmental threats that could affect system availability |
| Process integrity | - Maintain accurate records of system inputs and outputs - Implement procedures to quickly identify and correct system errors - Define processing activities to ensure products and services meet specifications |
| Confidentiality | - Identify and protect confidential information - Establish policies for data retention periods - Implement secure methods for destroying confidential data after retention periods expire |
| Privacy | - Obtain consent before collecting sensitive personal information - Communicate privacy policies clearly and in plain language - Collect data only through legal means and from reliable sources |
Note that these requirements are not one-time achievements, but rather a continuous process. Auditors will require control effectiveness over time.
How to achieve and maintain the security requirements
GitLab provides several features off the board to get you started with assuring SOC 2 security needs are met:
| Security Requirement | Addressing Feature |
|---|---|
| Implement controls to protect against unauthorized access | - Confidential Issues and Merge Requests - Custom Roles and Granular Permissions - Security Policies - Verified Commit - Signed Container Images - CodeOwners - Protected Branches |
| Set up systems for detecting and addressing security incidents | - Vulnerability Scanning - Merge Request Security Widget - Vulnerability Insights Compliance Center - Audit Events - Vulnerability Report Dependency List - AI: Vulnerability Explanation - AI: Vulnerability Resolution |
| Establish procedures for identifying and mitigating risks | All the above tools can be used by a security team to establish a procedure around what to do when security vulnerabilities are identified and how they are mitigated. |
Let’s go through each section and highlight the security features that address these requirements. Note that a GitLab Ultimate subscription and the correct Role and Permissions are required to access many of the features listed. Be sure to check out the appropriate documentation for more information.
Implement controls to protect against unauthorized access
Implementing robust access controls is essential for protecting an organization's assets, ensuring regulatory compliance, maintaining operational continuity, and fostering trust. GitLab allows you to implement controls to follow the principle of least privilege, securing against unauthorized access. This includes:
- Security policies
- Custom roles and granular permissions
- Branch protections and CodeOwners
- Verified commits
Security policies
GitLab's security policies, known as guardrails, enable security and compliance teams to implement consistent controls across their organization, helping prevent security incidents, maintain compliance standards, and reduce risk by automatically enforcing security best practices at scale.
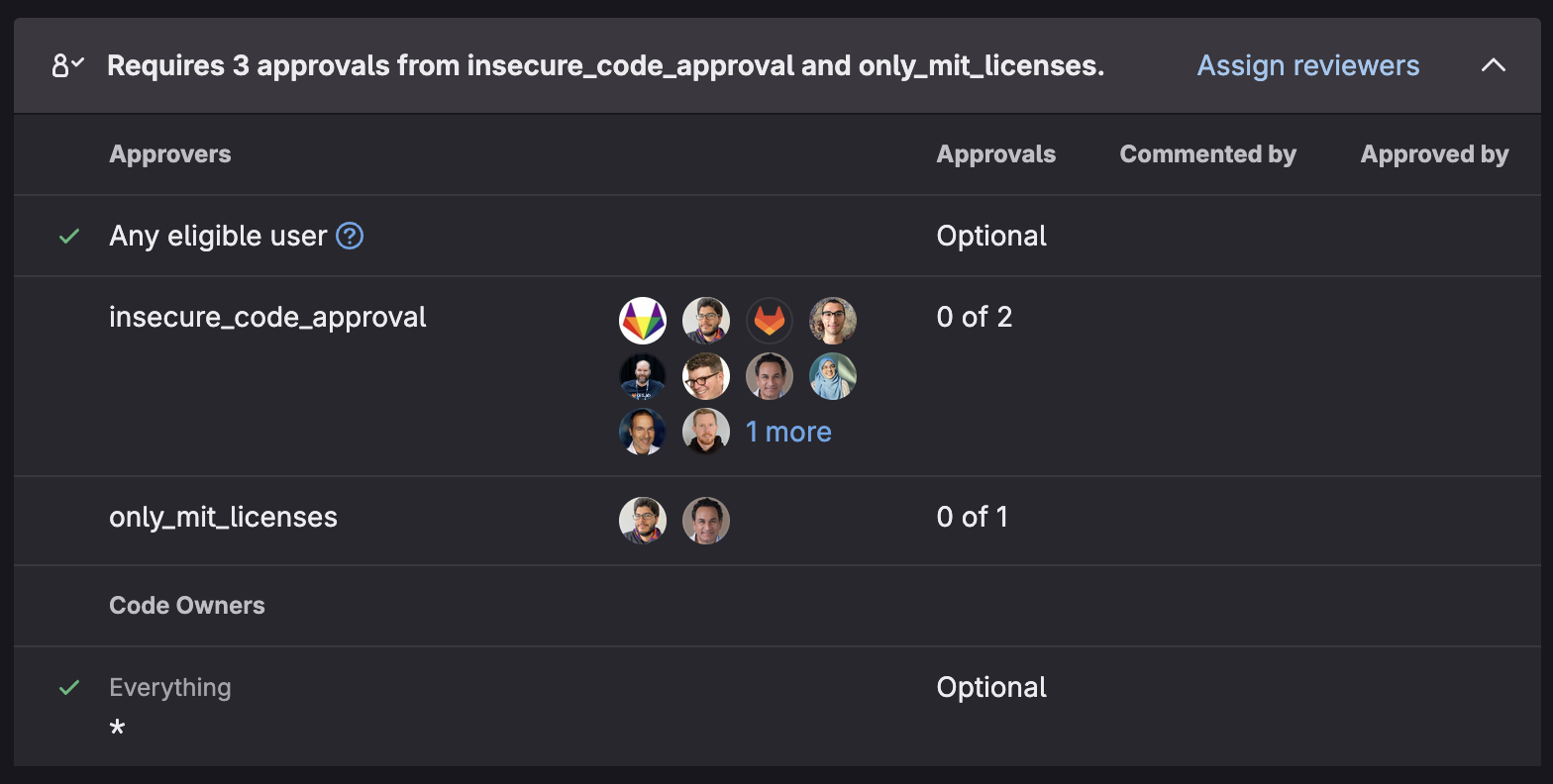
The following policy types are available:
- Scan execution policy
- Merge request approval policy
- Pipeline execution policy
- Vulnerability management policy
Learn how to create security policies with our security policy documentation.
Custom roles and granular permissions
Custom permissions in GitLab allow organizations to create fine-grained access controls beyond the standard role-based permissions.
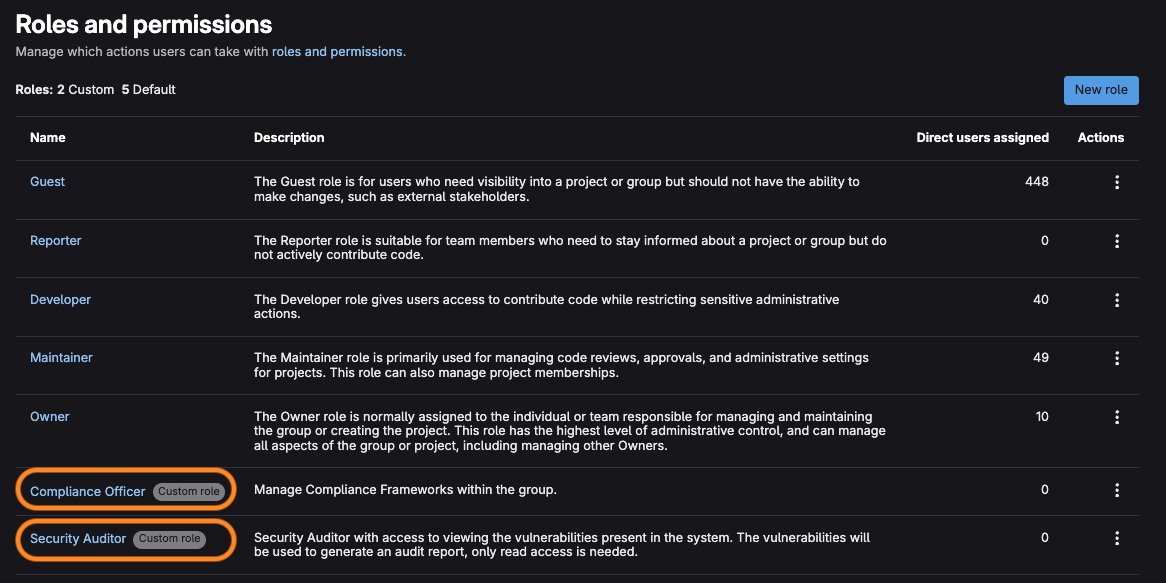
Learn how to create custom roles with granular permissions using our custom role documentation.
Branch protections and CodeOwners
GitLab helps you further control who can change your code using two key features:
- Branch Protection, which lets you set rules about who can update specific branches – like requiring approval before merging changes.
- Code Ownership, which automatically finds the right people to review code changes by matching files to their designated owners.
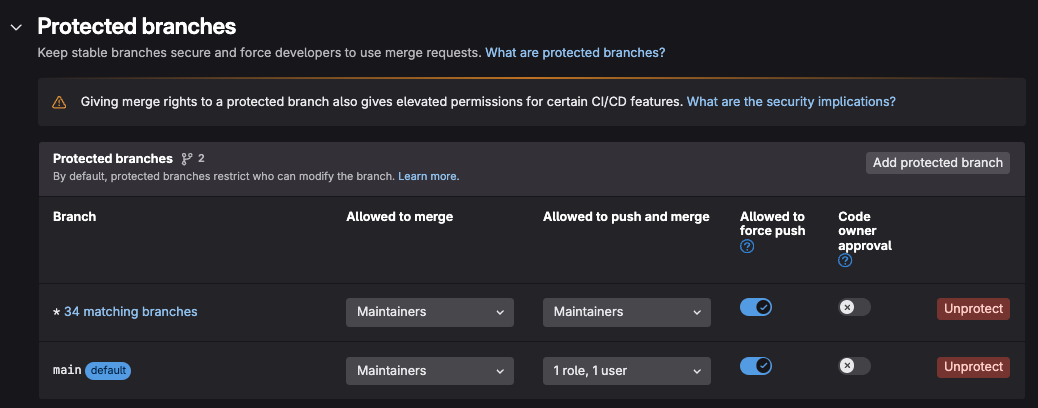
Learn how to create protected branches along with CodeOwners using protected branch and codeowner documentation.
Verified commits
When you sign your commits digitally, you prove they really came from you, not someone pretending to be you. When you upload your public GPG key to GitLab, it can check this stamp. If the stamp matches, GitLab marks your commit as Verified.
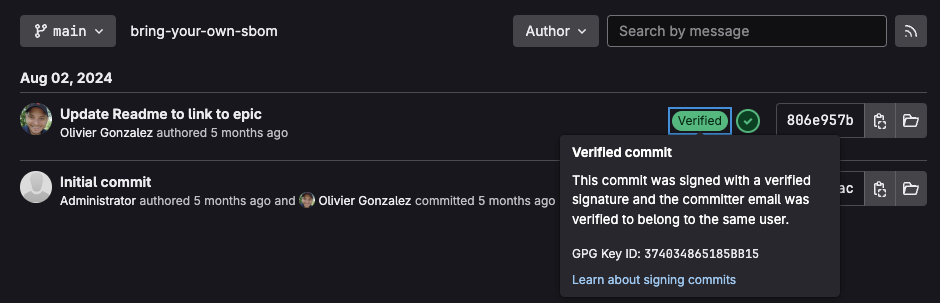
Learn more about verified commits with our signed commits documentation.
Set up systems for detecting and addressing security incidents
Setting up systems for detecting and addressing security incidents is vital for maintaining a robust security posture.
Security scanning and vulnerability management
GitLab provides a variety of security scanners that cover the complete lifecycle of your application:
- SAST
- DAST
- Container Scanning
- Dependency Scanning
- IaC Scanning
- Coverage-guided Fuzzing
- Web API Fuzzing
Example .gitlab-ci.yml setup:
stages:
- test
include:
- template: Jobs/Dependency-Scanning.gitlab-ci.yml
- template: Jobs/SAST.gitlab-ci.yml
These jobs are configurable via environment variables. Once a pipeline runs, vulnerabilities appear directly in merge requests with detailed information, allowing for early detection and remediation.
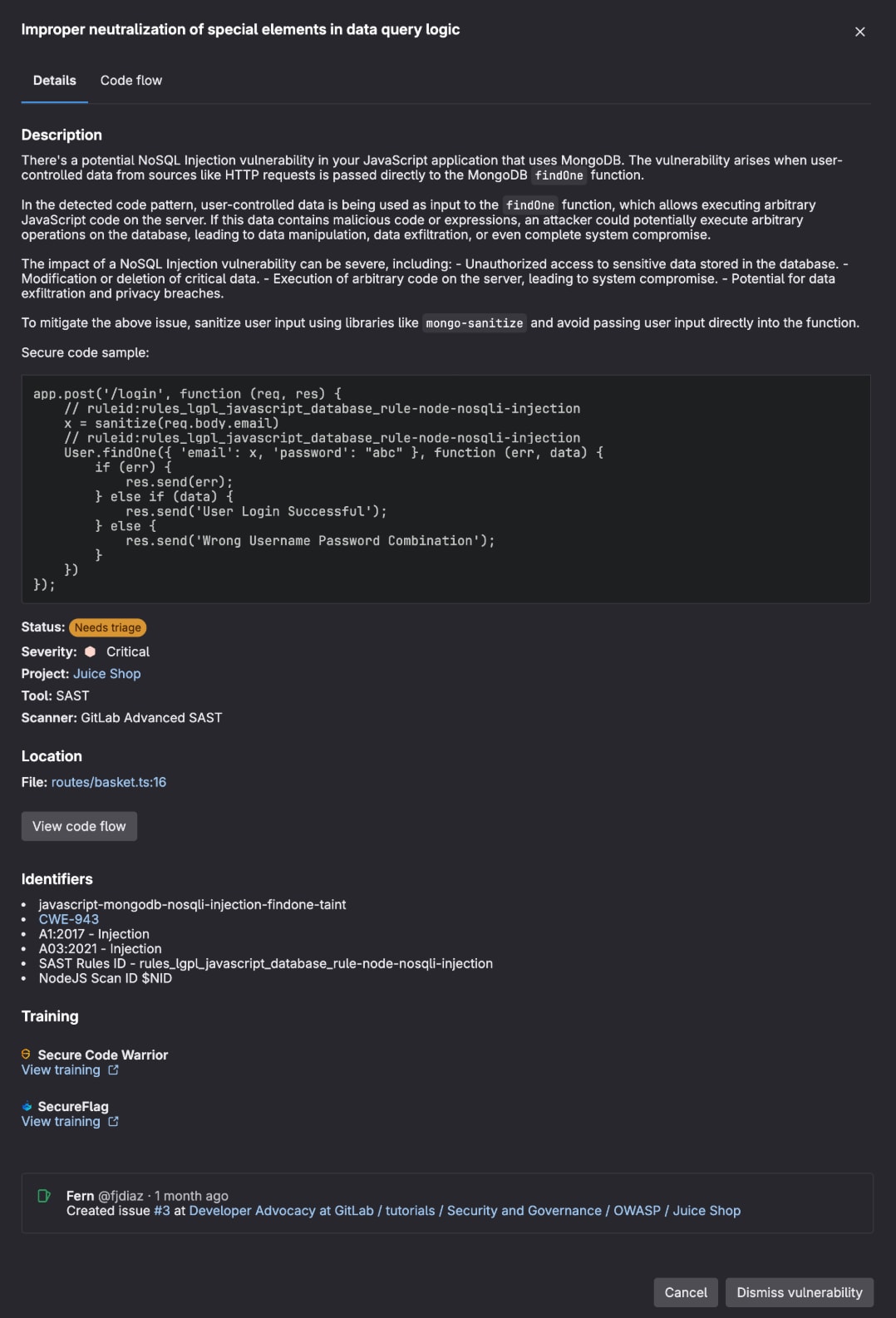
Learn more in our application security documentation.
Software bill of materials
GitLab can generate a Software Bill of Materials (SBOM), providing visibility into dependencies, versions, and known vulnerabilities.
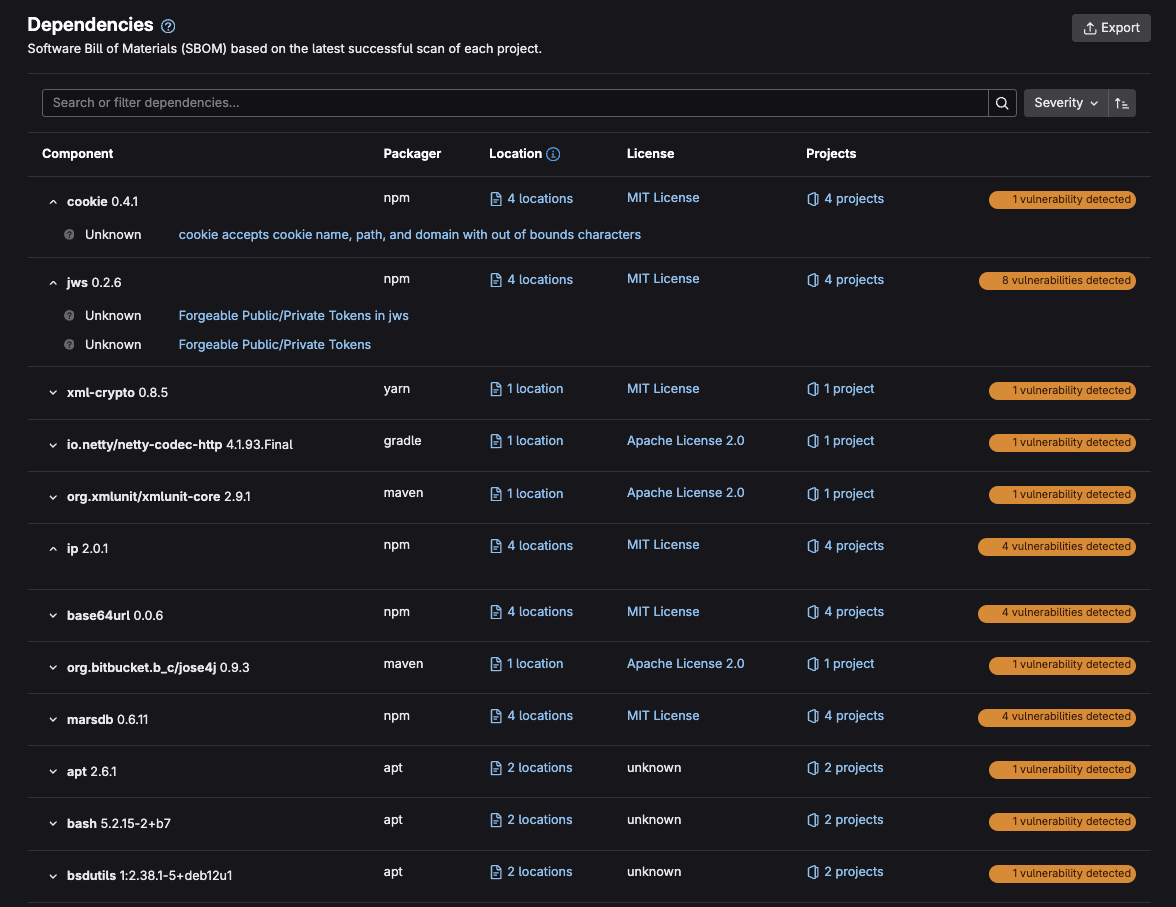
Learn how to use the dependency list documentation.
System auditing and security posture review
GitLab's audit events log all changes across projects, providing traceability and accountability.
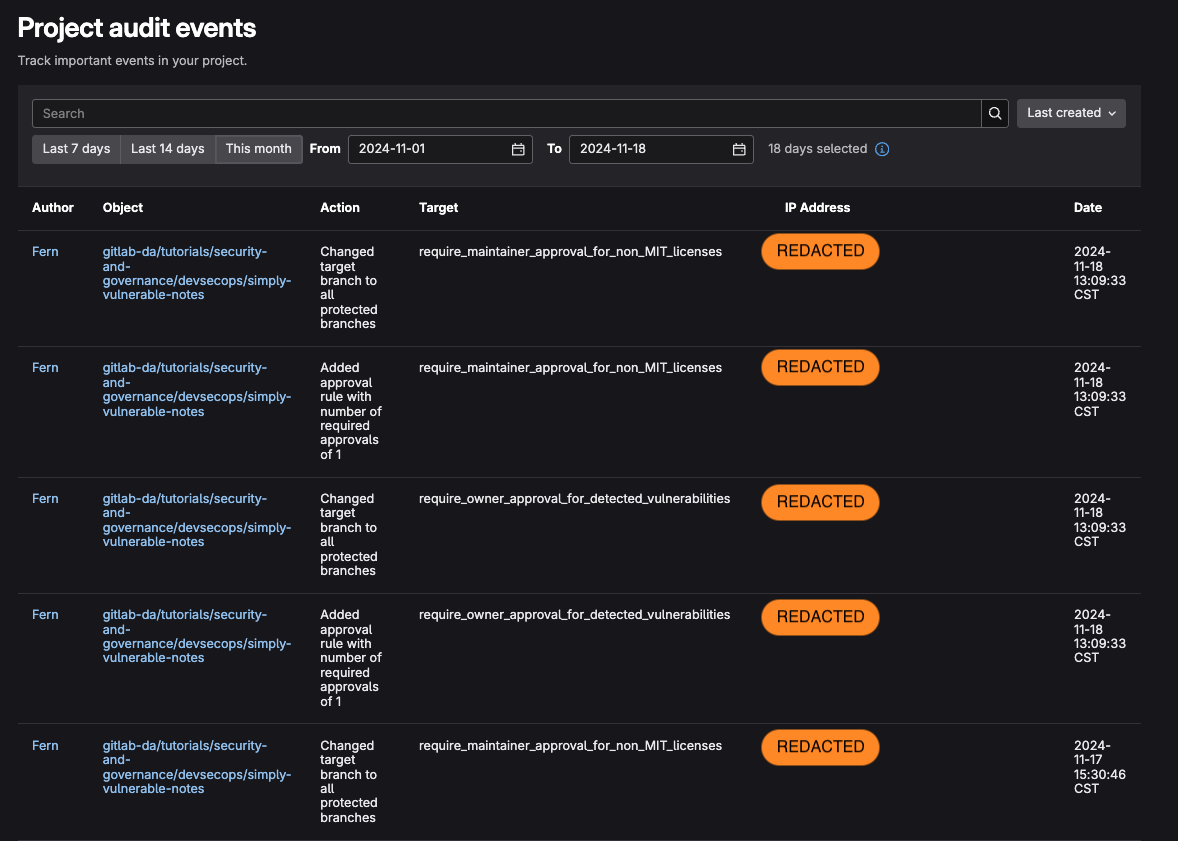
Learn more in the audit events documentation.
Compliance and security posture oversight
GitLab’s Security Dashboard aggregates results from all scanners, giving visibility across projects.
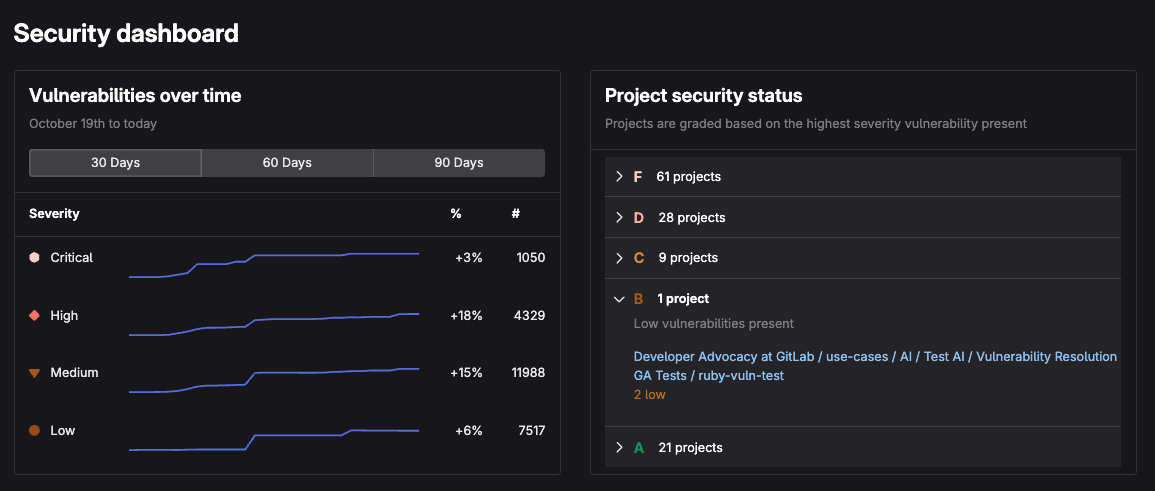
Learn more in the security dashboard documentation.
Establish procedures for identifying and mitigating risks
Vulnerabilities go through a specific lifecycle. GitLab helps enforce procedures like requiring approval for merging vulnerable code, prioritizing vulnerabilities by severity, and validating fixes using scanners and tests.
Best practices for SOC 2 compliance
- Establish a strong security culture.
- Document policies, procedures, and controls.
- Automate where possible.
- Communicate effectively with stakeholders.
- Seek expert guidance when needed.
Achieving SOC 2 compliance is a significant undertaking, but by leveraging GitLab’s built-in security and compliance tools, organizations can streamline the process, reduce risk, and demonstrate trust to customers.
Read more
We want to hear from you
Enjoyed reading this blog post or have questions or feedback? Share your thoughts by creating a new topic in the GitLab community forum.
Share your feedback
